IoT devices are transforming modern businesses and bringing greater efficiency, but they also deserve careful attention when it comes to security.
From medical monitors and factory sensors to smart cameras, IoT devices have become an essential part of today’s hospitals, factories, and office buildings. While they boost efficiency and enable automation, they also introduce new security risks. Many of these devices are difficult to update, lack even basic protection, and are hidden deep within the network without proper segmentation. A single compromised device can open the door to serious damage.
To help you secure your IoT environment, we’ve compiled a set of essential best practices, along with guidance on how GREYCORTEX Mendel can help you put them into action through enhanced visibility, monitoring, and detection.
Best Practices to Protect Your IoT Ecosystem with Mendel
With the right foundations in place, securing your IoT environment becomes manageable. Below, we break down key practices to strengthen visibility, control, and response, and show you how each one can be implemented and visualized using GREYCORTEX Mendel.
Map all IoT devices and assess their risks
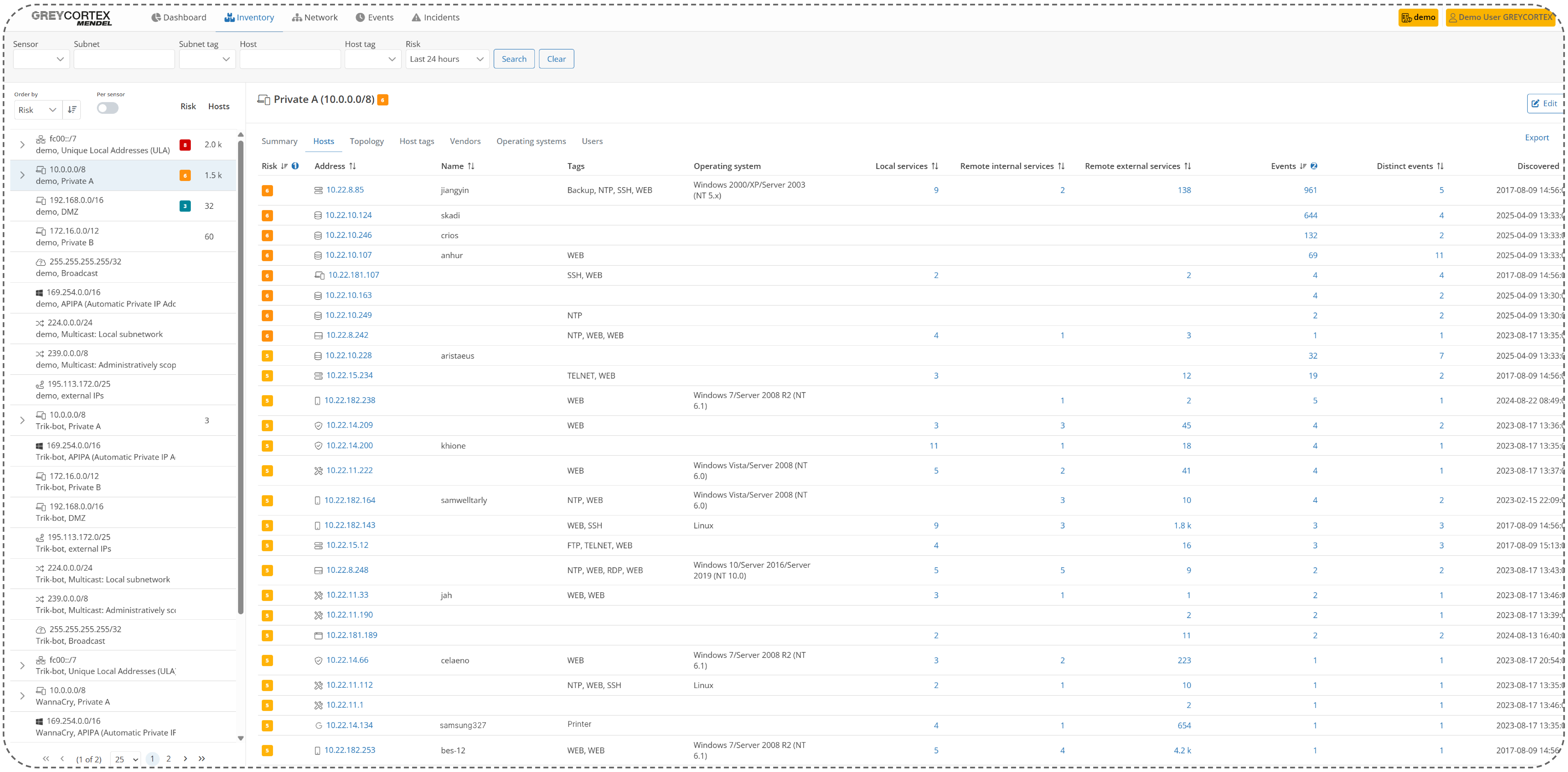
Start by identifying every IoT device connected to your network—smart sensors, medical equipment, and other smart devices. Once you can see the full picture, assess which devices are critical, which are exposed, and what could happen if one of them gets compromised. Not all devices need the same level of protection, but all need to be accounted for.
Steps to take:
- Scan your network to identify all connected devices
- Document IPs, MAC addresses, models, locations, and owners
- Classify devices based on criticality and exposure
- Evaluate known vulnerabilities
Mendel in practice
In Mendel’s inventory tab, you get a real-time view of all active devices in your network, automatically mapped to their segments. For each device, you can see critical details like IP address, hostname, OS, and the severity of detected events. Mendel also tags hosts (e.g., AD server, printer), helping you quickly identify their role and assess their risk level.
Segment your network and control access
Use network segmentation to separate IoT devices from other networks and enforce access controls to limit unnecessary communication. A hospital X‑ray should reside in a protected clinical segment, while non-critical devices such as smart lighting must be isolated from sensitive systems like medical records or operational platforms.
Steps to take:
- Group devices into segments by purpose, location, and risk
- Define strict access policies among segments
- Use firewalls, VLANs, or SDN to enforce segmentation
- Regularly review and update access rules
Mendel in practice
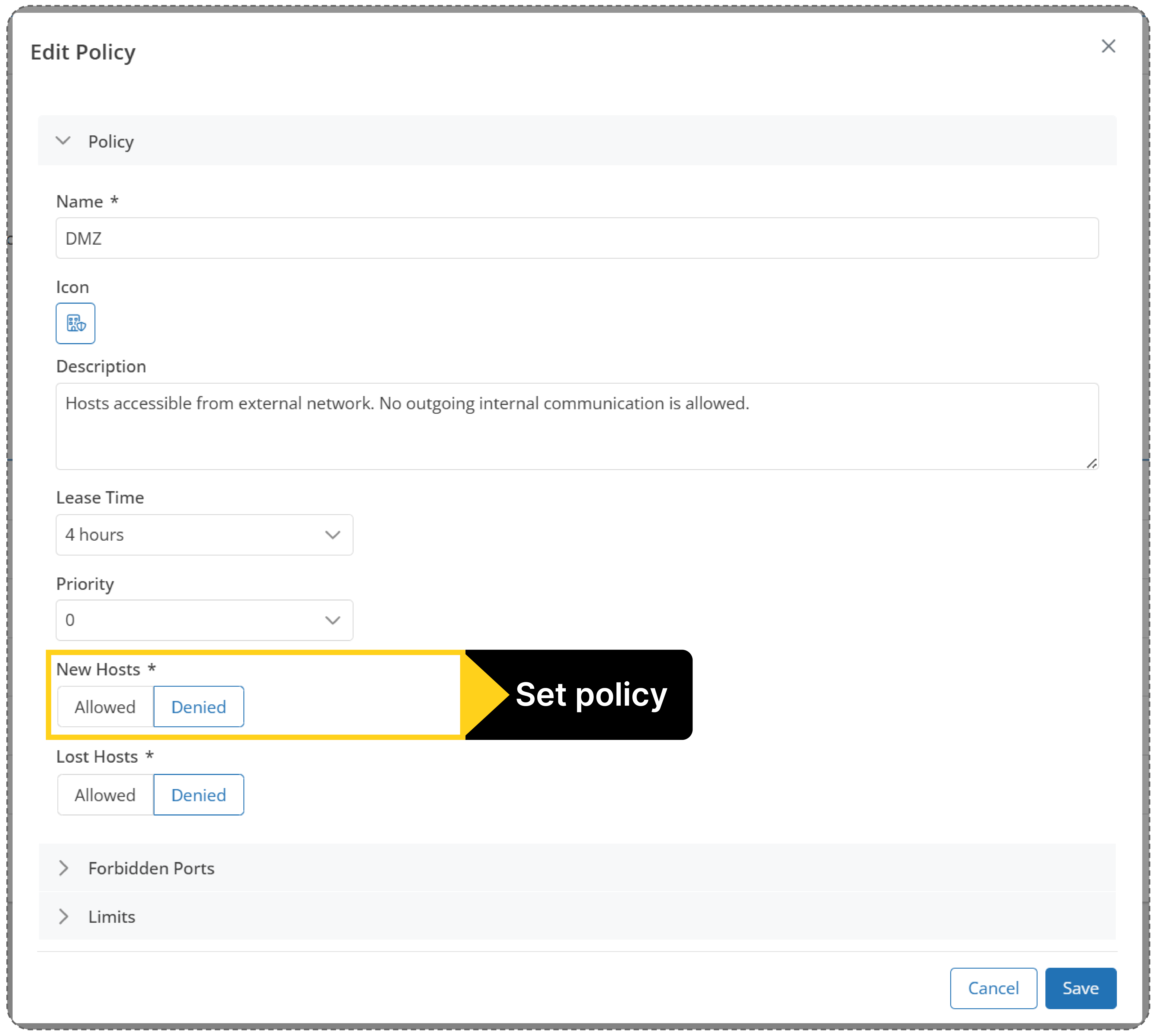
Mendel provides a clear view of all internal communications, allowing you to ensure each IoT device communicates only with approved segments. This helps maintain proper isolation and enforces your segmentation strategy.
For critical network segments, Mendel lets you define custom rules to alert you immediately when an unknown device connects. This real-time visibility enables fast response and strengthens your access control.
Monitor and detect threats across your network
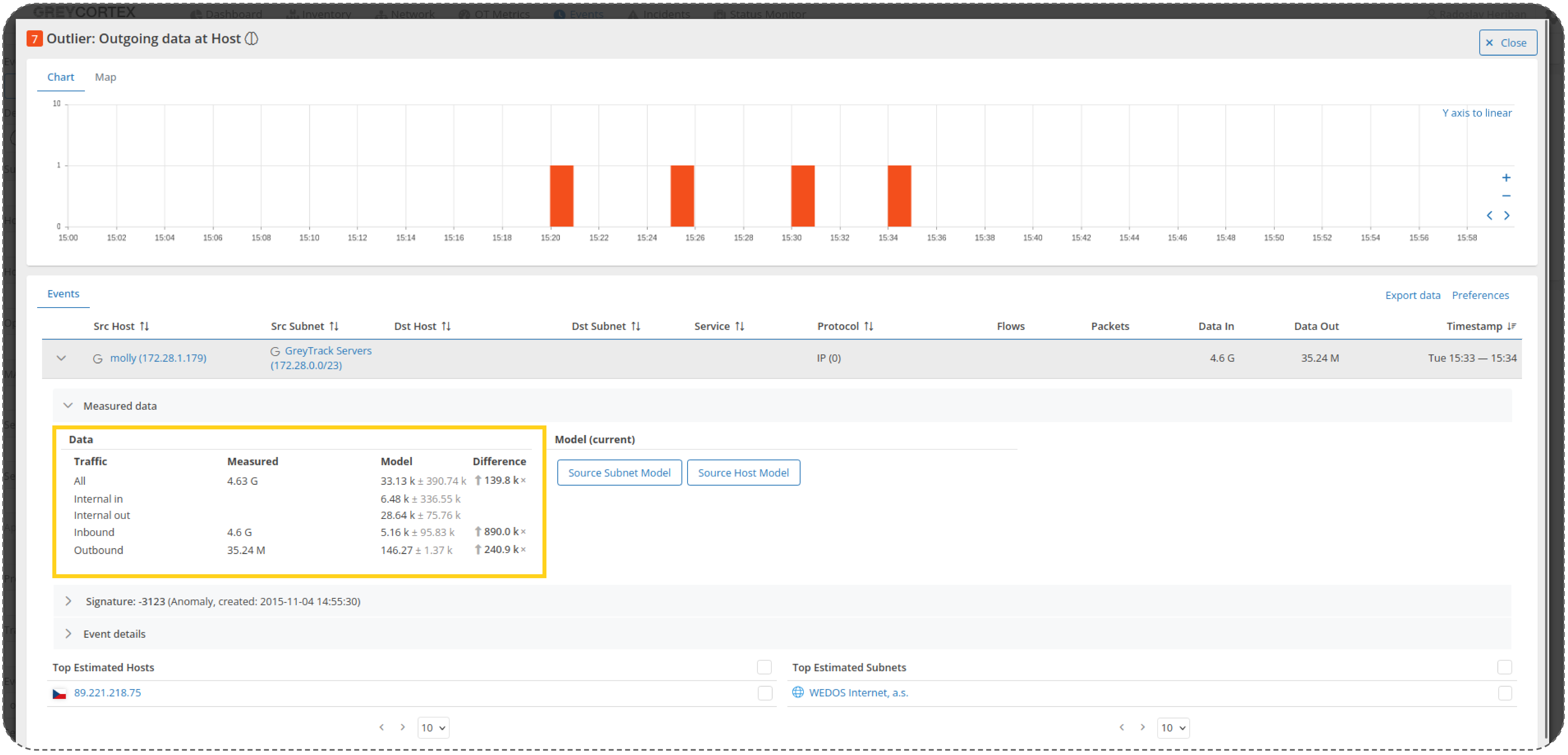
Even properly configured devices can become a risk. Continuous monitoring provides real-time visibility into IoT communication patterns, revealing who connects, when, and how often. With behavioral baselines in place, you can quickly detect anomalies, unauthorized access, or lateral movement attempts before they escalate.
Steps to take:
- Monitor all traffic to and from IoT devices
- Investigate anomalies like new destinations, large data transfers, or off-hours activity
- Flag port scans or sudden traffic spikes from low-profile devices
Mendel in practice
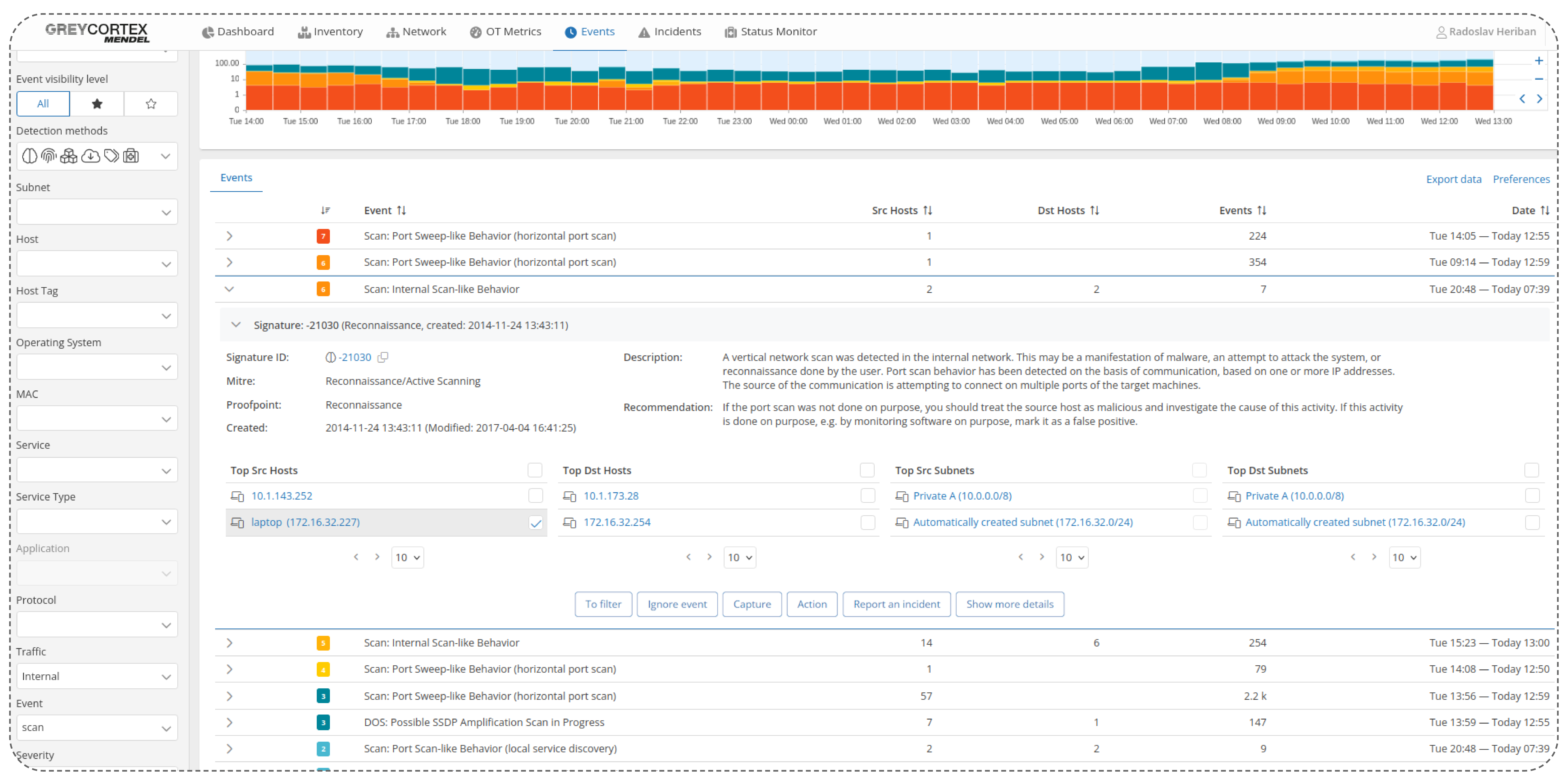
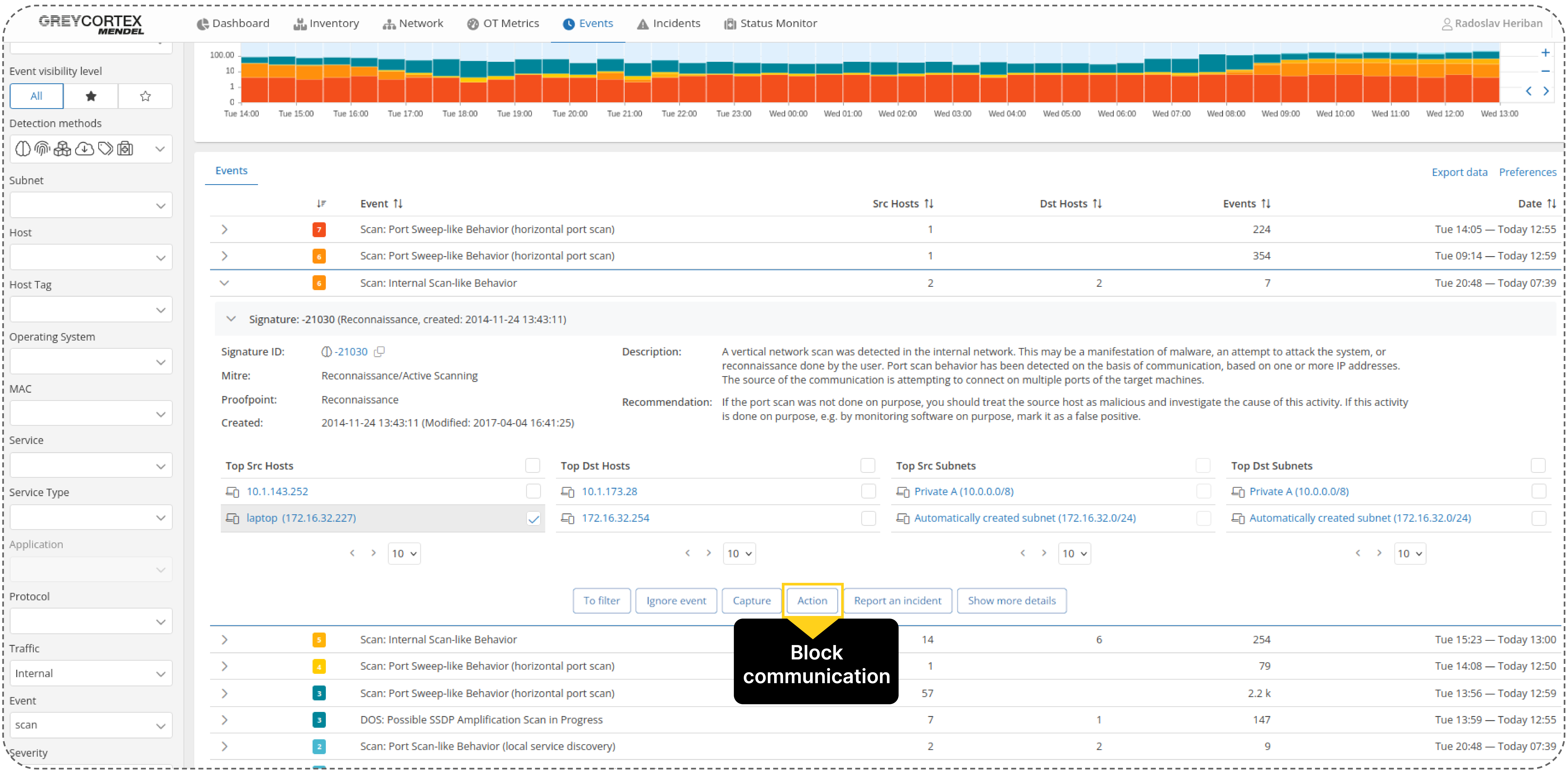
Mendel automatically detects suspicious patterns like port scanning. If an IoT device suddenly starts reaching out to unusual services or systems, Mendel alerts you to possible malware activity or an attacker mapping your network.
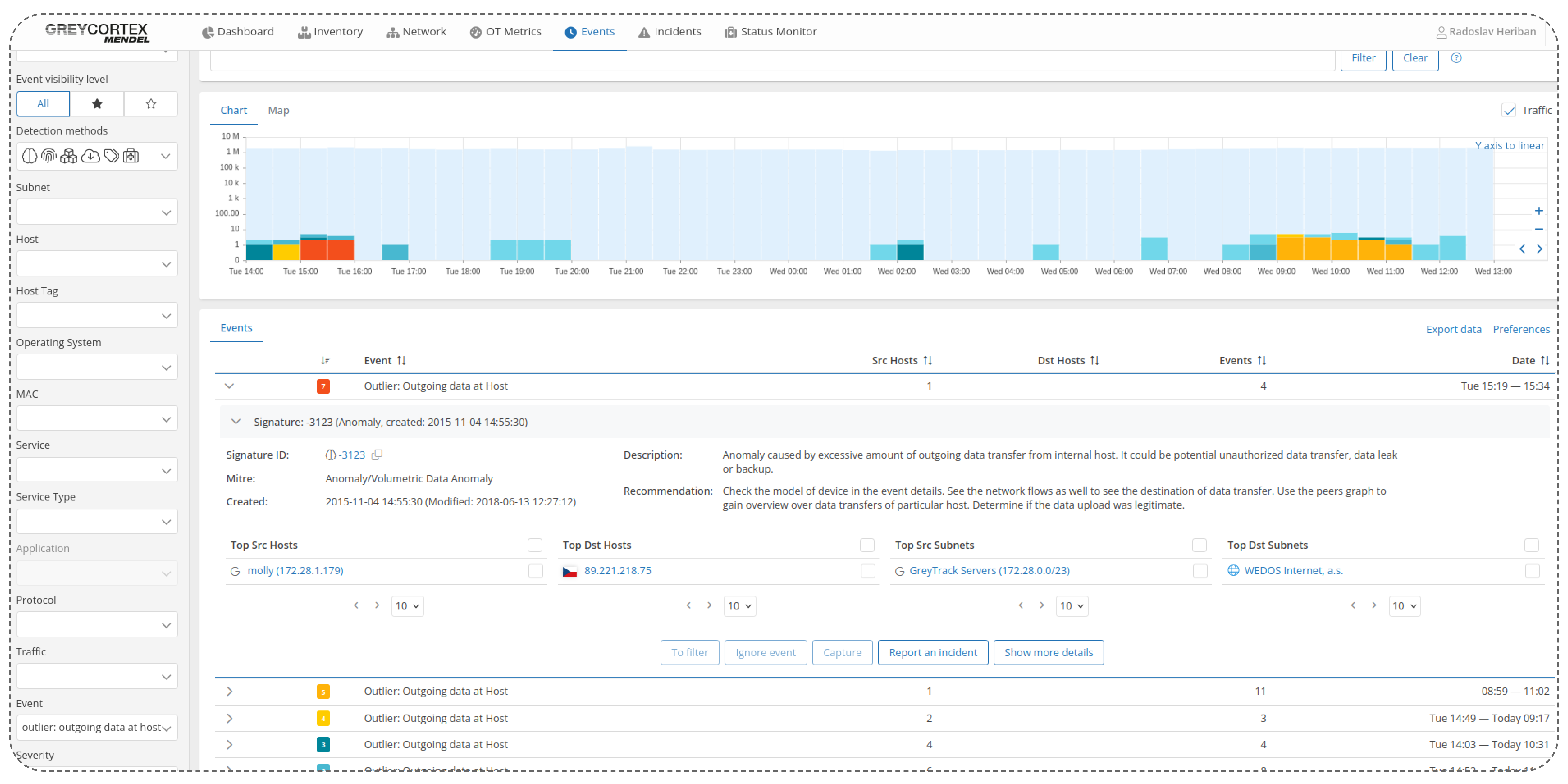
Mendel monitors data flows and alerts you to anomalies. If a device suddenly begins transferring large volumes of data, especially to unfamiliar destinations, it could signal a compromise. Early detection helps you respond before any damage is done.
Prepare an incident response plan
When an unauthorized IoT device appears on your network, time matters. Having a clear response plan helps you react quickly by isolating the device, understanding its behavior, and preventing further damage without losing precious time to confusion.
Steps to take:
- Establish automated alerts
- Assign roles and responsibilities for investigation and containment
- Log all actions for future analysis and compliance
Mendel in practice
When Mendel detects suspicious activity from an IoT device, you can respond immediately—either manually or through automated rules. Block malicious traffic via integrated firewalls or isolate compromised devices using your NAC system to prevent further impact.
Build a Resilient IoT Environment with Mendel
IoT devices do not have to be your weakest link. With a clear inventory, proper segmentation, and real-time monitoring, you can reduce exposure and respond to threats before they escalate.
GREYCORTEX Mendel helps you put described practices into action. It gives you a complete picture of device activity, lets you detect unusual behavior early, and supports quick, informed responses. As IoT continues to grow across industries, having this level of control makes a big difference in keeping your network stable, secure, and ready for what’s next.
Categories
- Company News (35)
- Product News (27)
- IT/OT Security (39)
- Webinars (6)