Defining your internal network policies takes time, coordination, and effort. But once those policies are in place, the critical question still remains: are they actually being followed?
For many IT teams, verifying policy adherence and enforcing internal rules on a daily basis is a persistent challenge. Even small violations, such as unauthorized access, outdated encryption, or misused services, can lead to data exposure or non-compliance with frameworks like NIS2.
This is the first part of a two-part blog focused on the practical side of network security policy enforcement and explains how GREYCORTEX Mendel helps you detect violations of any size quickly and effectively. Part two will cover encryption, application use, and identity-based access control.
🔗 Read Part 2 to continue exploring how Mendel supports effective policy enforcement and risk mitigation.
Network Segmentation & Perimeter Control
Segmentation and perimeter access policies are fundamental to limiting exposure and maintaining control over your critical systems. Without a clear policy enforcement process, a single compromised device can lead to lateral movement across your network.
🔗 Watch our webinar to see how Mendel helps you detect and investigate lateral movement.
Policy violation: Unallowed east–west traffic between segments
Relevant for NIS2
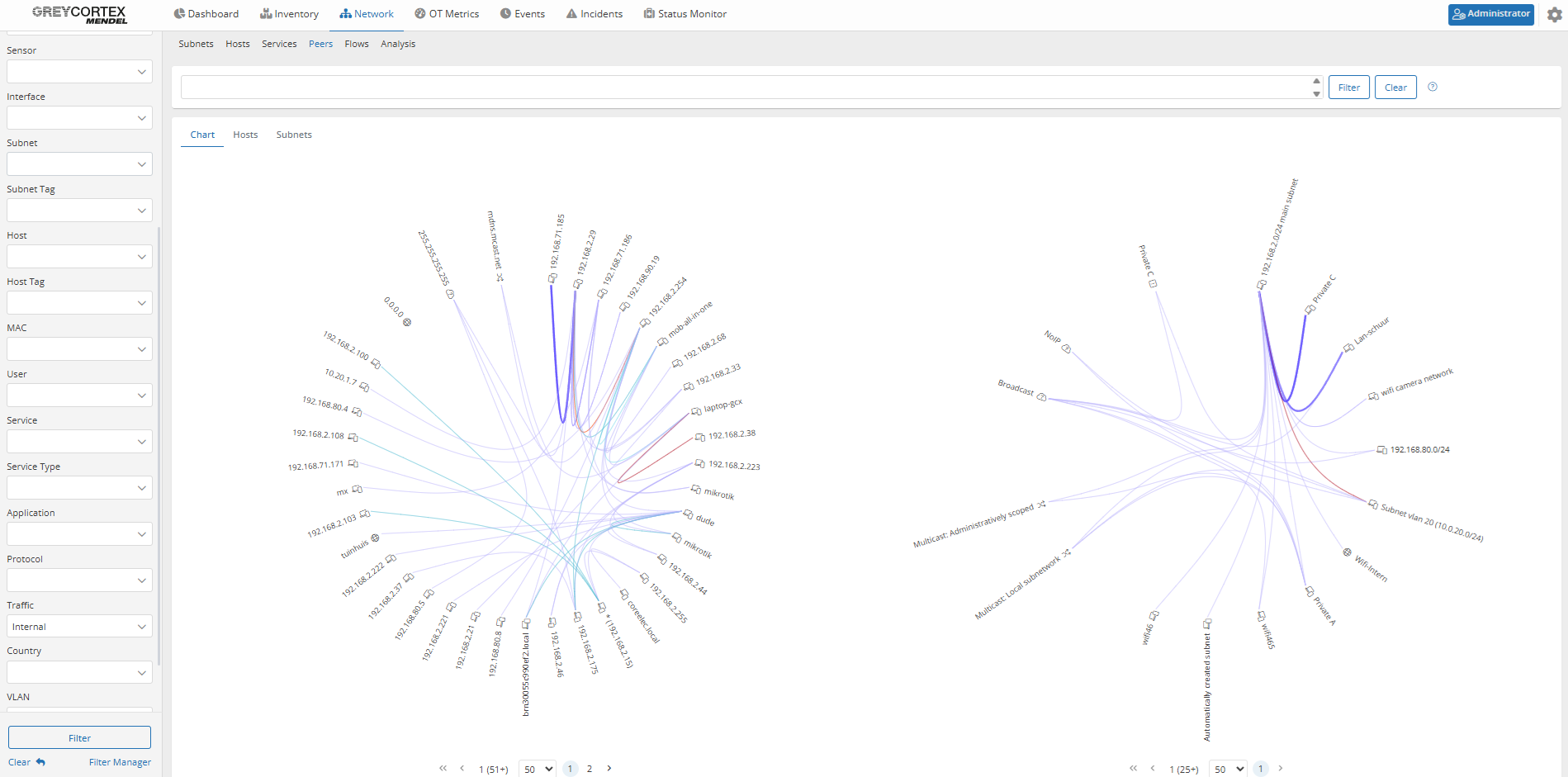
East–west traffic refers to communication between devices within the internal network, such as between user devices and servers. When segmentation is not properly enforced, attackers can move laterally across segments and compromise your entire company network. Limiting this traffic is essential for helping you prevent access to critical systems.
Validation with Mendel
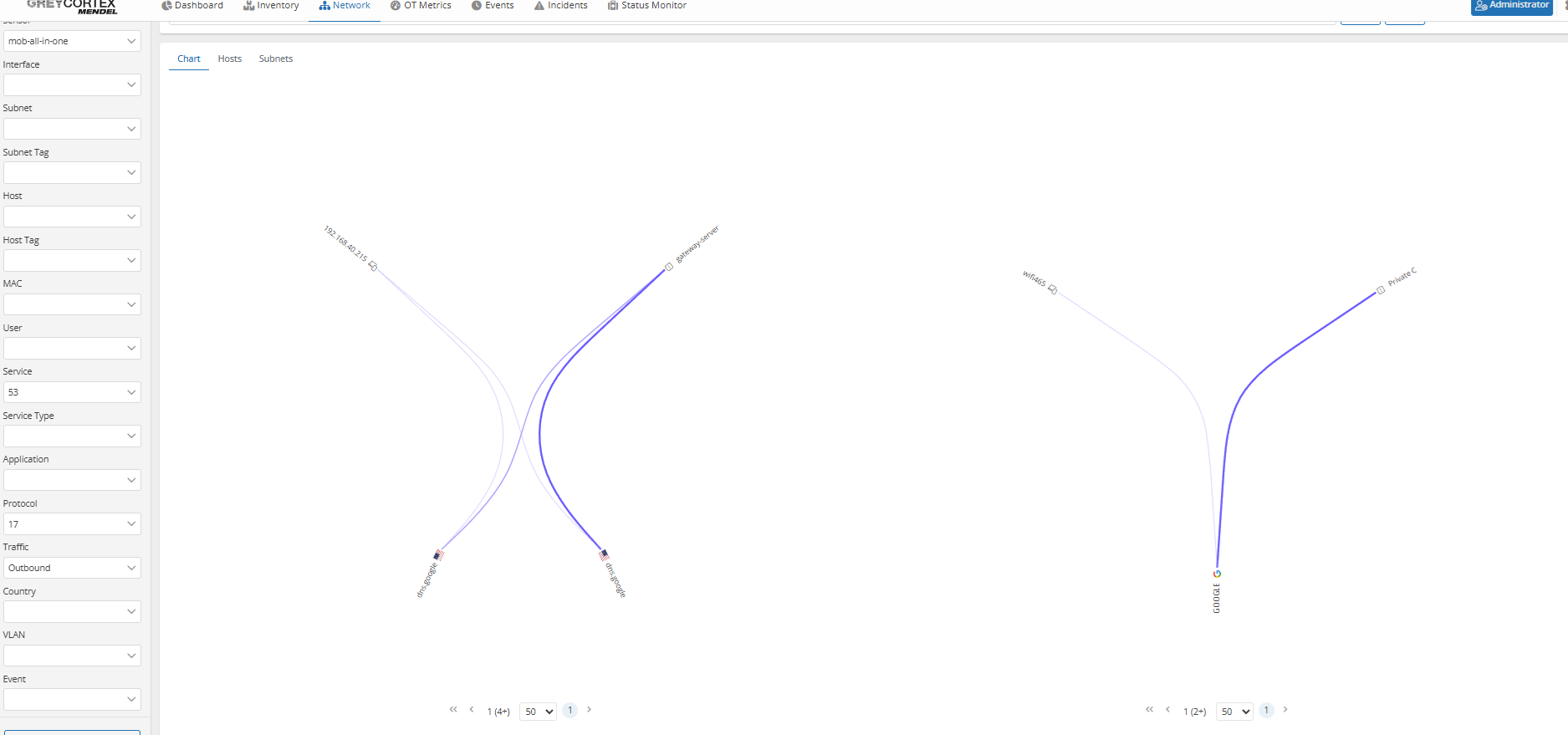
Mendel’s peer graph, as seen below, offers you a clear view of internal communication. Your analysts can then filter internal traffic and define specific subnets to quickly verify whether unauthorized flows occur between isolated segments.
Policy violation: Unauthorized Internet access from restricted segments
Relevant for NIS2
Devices in restricted segments, such as servers or backup networks, are often not intended to communicate with the public Internet directly. In many environments, internet access must go through a proxy or DMZ, with firewalls blocking all other outbound traffic. If these controls fail, systems may be exposed to malware, data leakage, or command-and-control activity.
Validation with Mendel
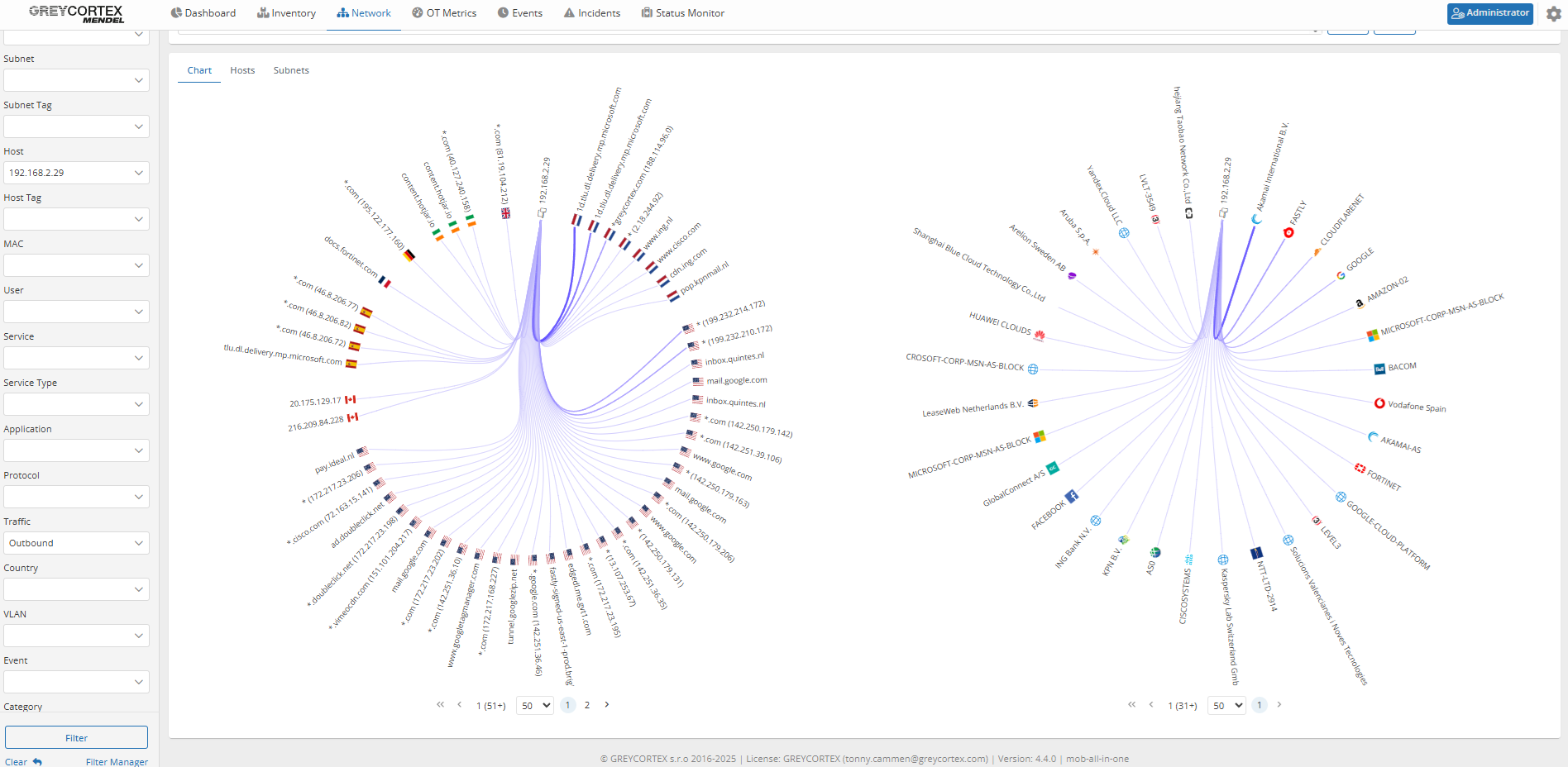
Mendel allows the filtering of your outbound traffic from specific hosts, making it easy to identify devices attempting to access the Internet.
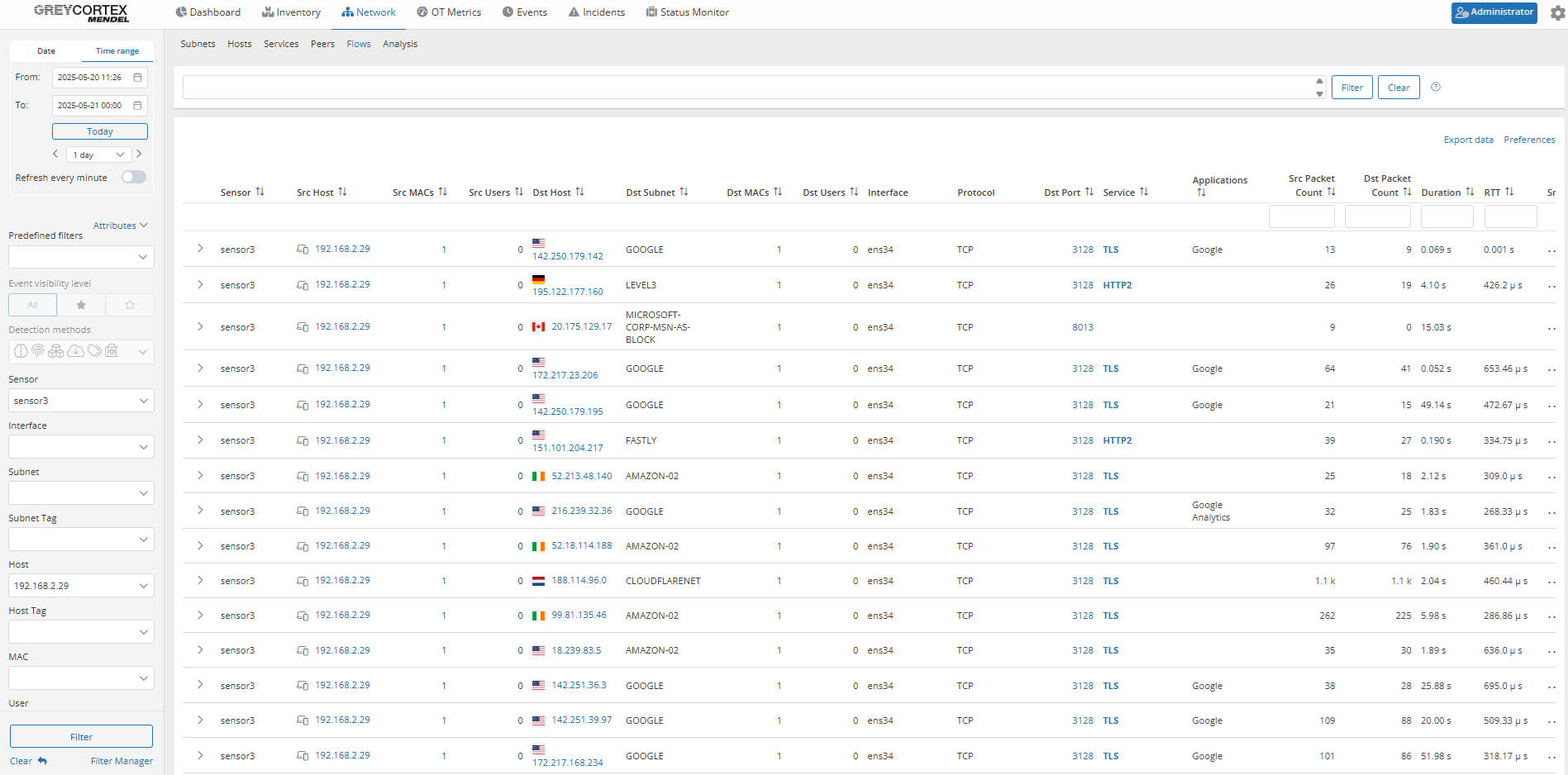
If such traffic is detected, your analysts can verify whether it passed through an approved proxy by checking the flow records. They can also confirm whether direct connections (bypassing the proxy) were blocked at the firewall level by checking the TCP flags and destination status.
Mendel lets you set policies to monitor Internet traffic from specific segments or devices. When a violation occurs, it automatically sends an alert.
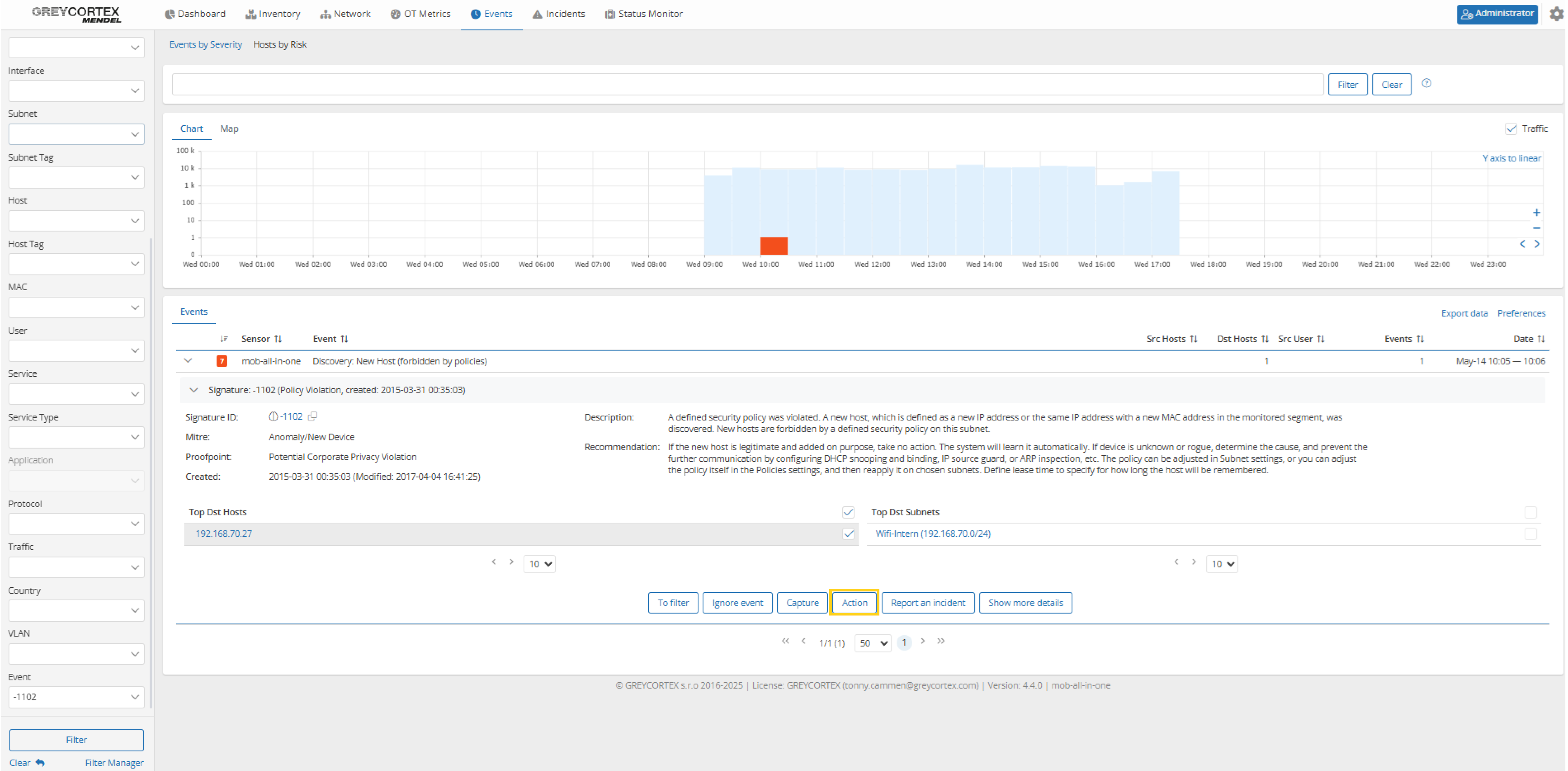
Policy violation: New & disappeared IPs or MACs in controlled network
Relevant for NIS2
Controlled network segments, such as server or infrastructure zones, are often designed with static IP and MAC configurations. When unrecognized devices appear, it may indicate unauthorized access, policy misconfiguration, or a potential threat.
Validation with Mendel
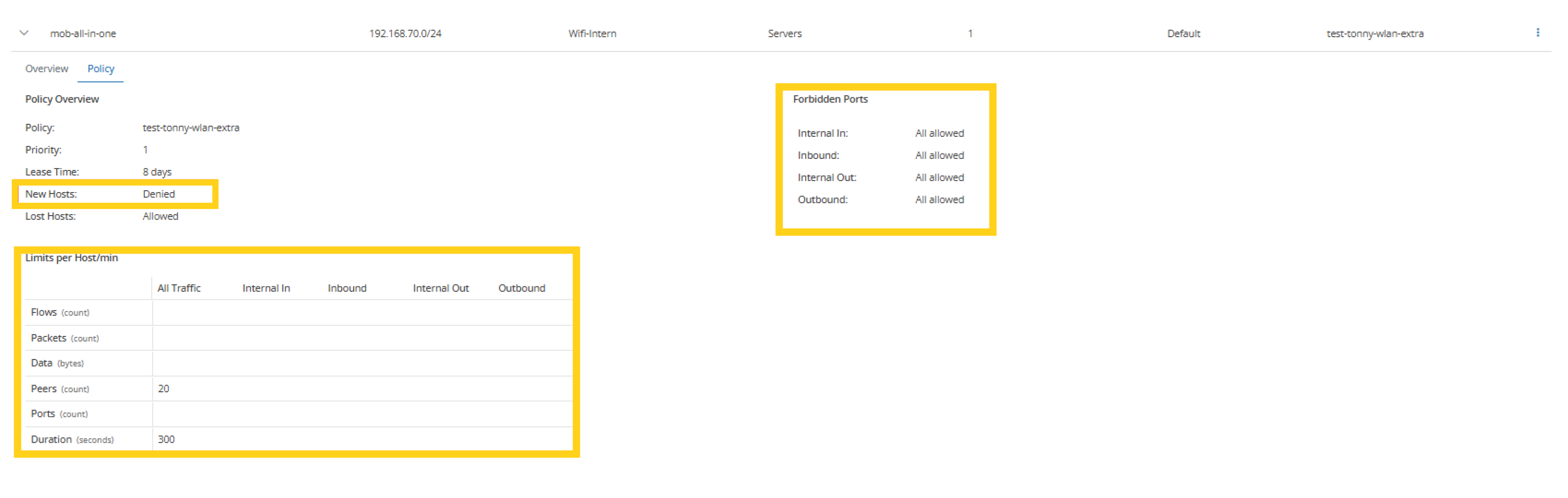
Mendel allows you to assign policies to specific subnets or hosts to monitor new or missing IP and MAC addresses. Policies can also include limits on traffic, packets, peers, ports, duration, and flows.
If a policy is violated, Mendel will trigger an alert immediately. For automated blocking, Mendel can be integrated with third-party systems like a NAC or Cisco ISE.
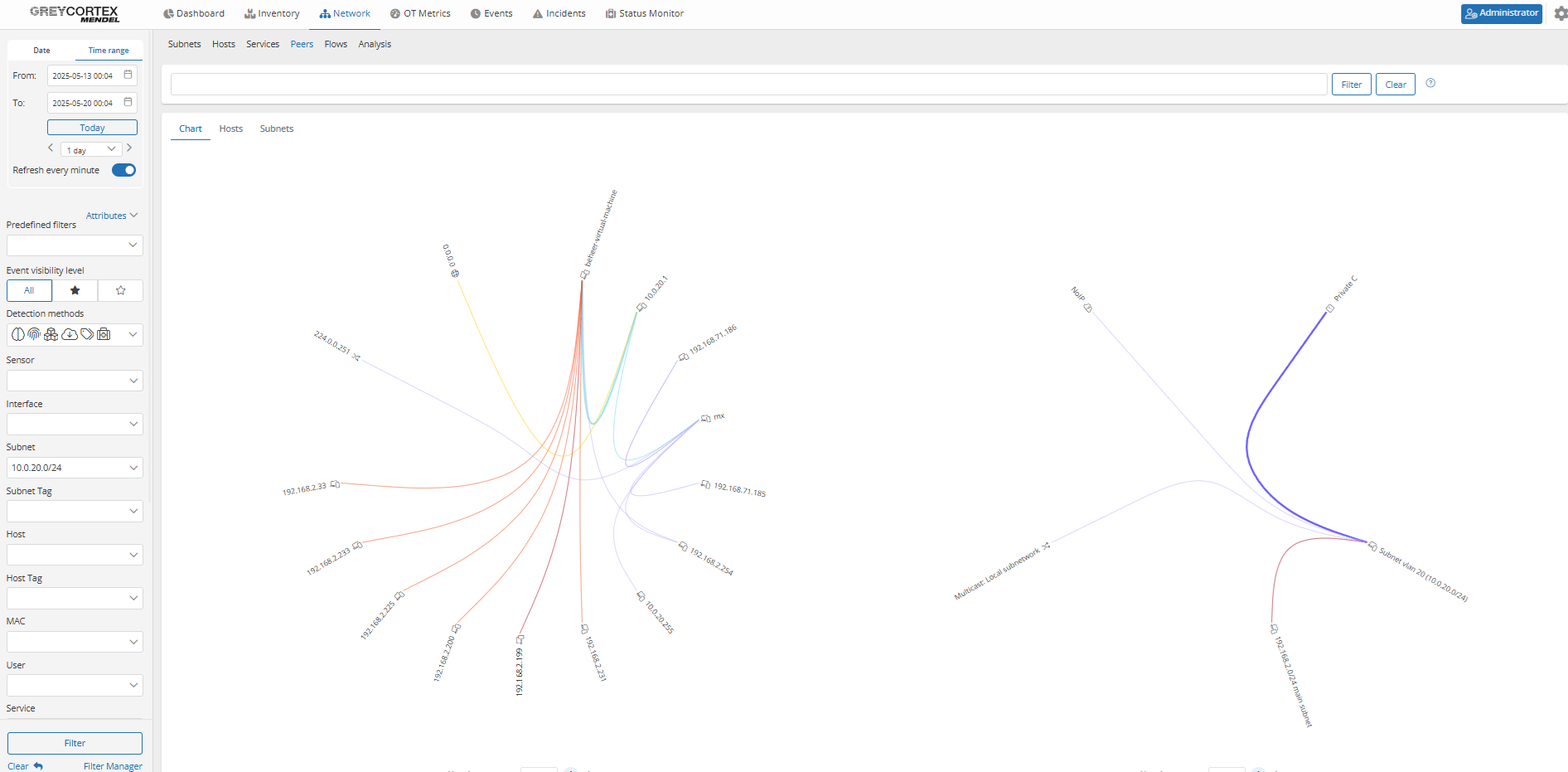
Policy violation: Improper traffic between management and user networks
Relevant for NIS2
Dedicated management segments are designed to limit who can interact with your infrastructure components like switches, routers, or servers. Unauthorized access from user networks increases the risk of misconfiguration, privilege abuse, or direct exploitation.
Validation with Mendel
Mendel’s peer graph provides you with a clear view of communication between your defined network segments. Your analysts can focus on management subnets to verify whether they are properly isolated from user networks, as required by internal policies.
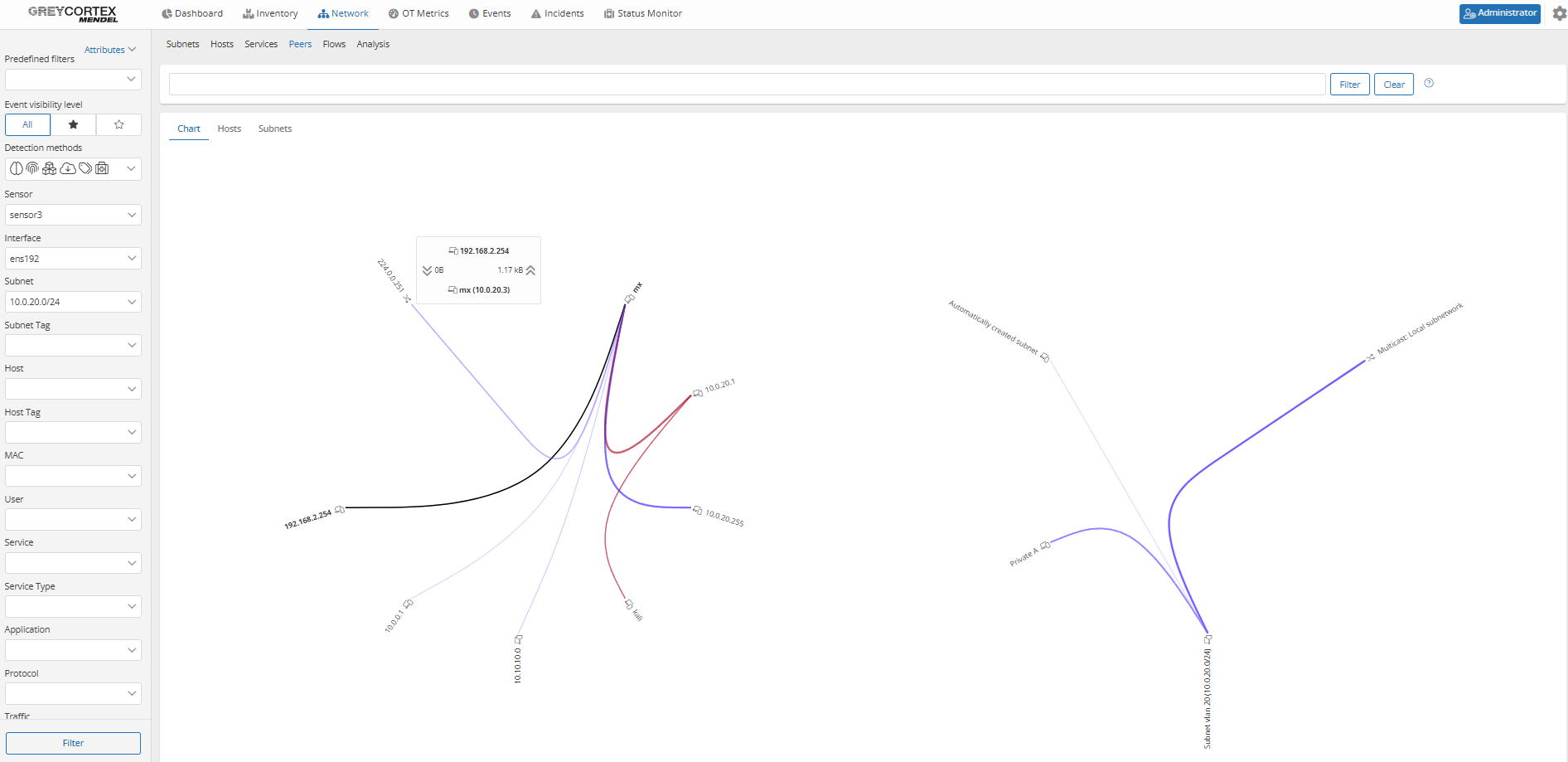
For example, subnet 10.0.20.0/24 was assigned as a management zone, but Mendel revealed active connections to other internal networks.
After updating firewall rules, Mendel confirms isolation by showing no communication from 10.0.20.0/24.
Network Services Policy Enforcement
Core network services like DNS and DHCP are frequent targets for misuse or misconfiguration. Ensuring that only authorized services are active helps prevent spoofing, data leaks, and disruptions to your network stability.
Policy violation: Usage of unauthorized internal/public DNS servers
Relevant for NIS2
This policy ensures that only approved DNS servers are used for resolving domain names inside the network. Unapproved or misconfigured servers can bypass security controls, hide malicious activity, or return forged responses.
Validation with Mendel
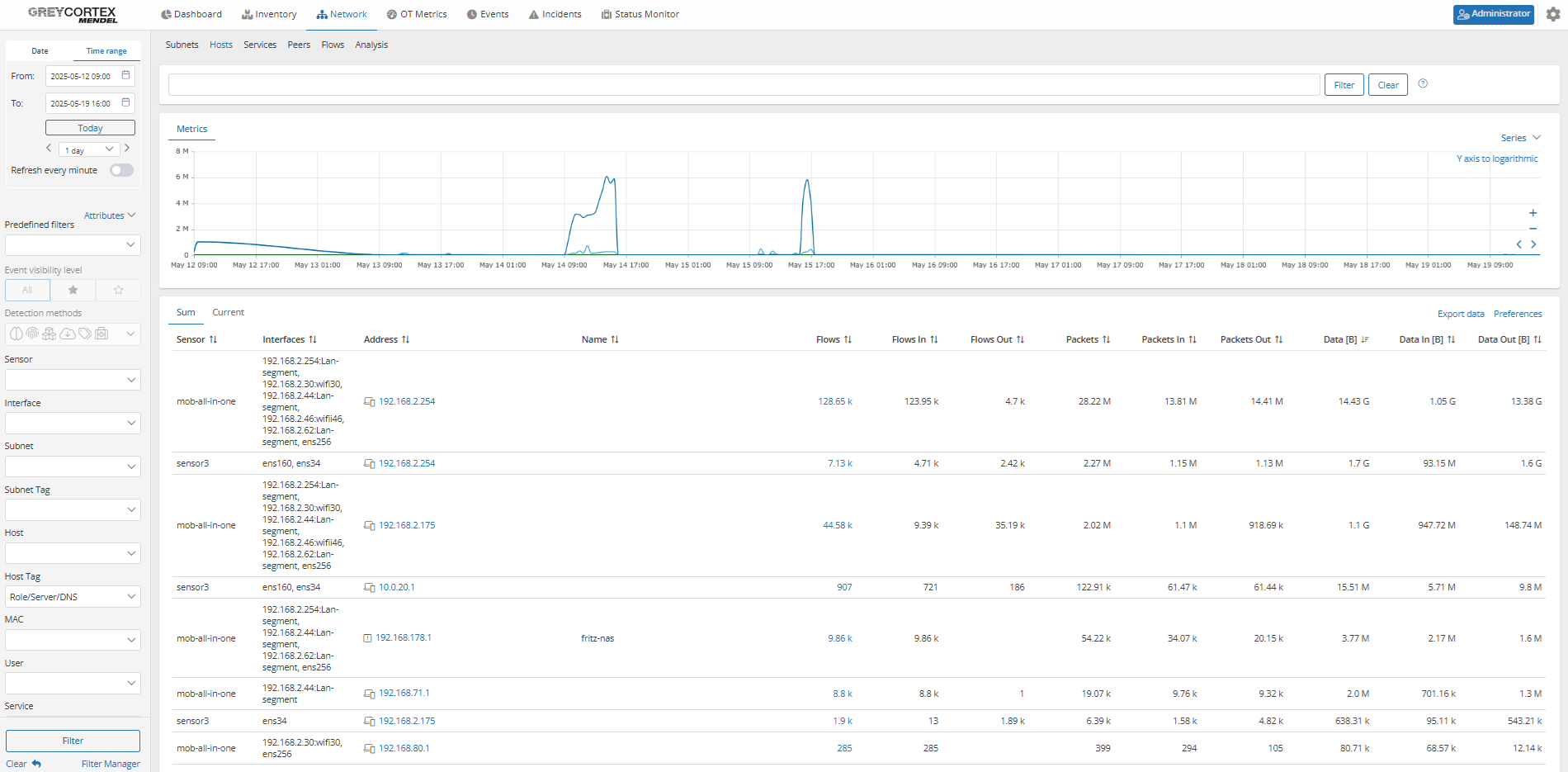
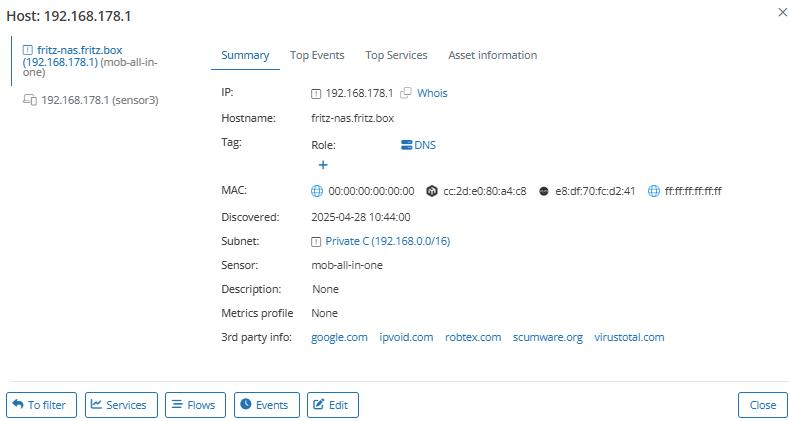
Internal DNS usage: Mendel allows you to filter internal DNS servers using the host tag Role/Server/DNS. This provides you with a clear inventory of devices offering DNS or DNS-relay services. Your analysts can review this list and drill down into individual IPs to confirm whether each DNS server is expected and approved.
For example, a device at 192.168.178.1 was identified as providing DNS services. No other services were detected, indicating a possible relay or misconfigured gateway.
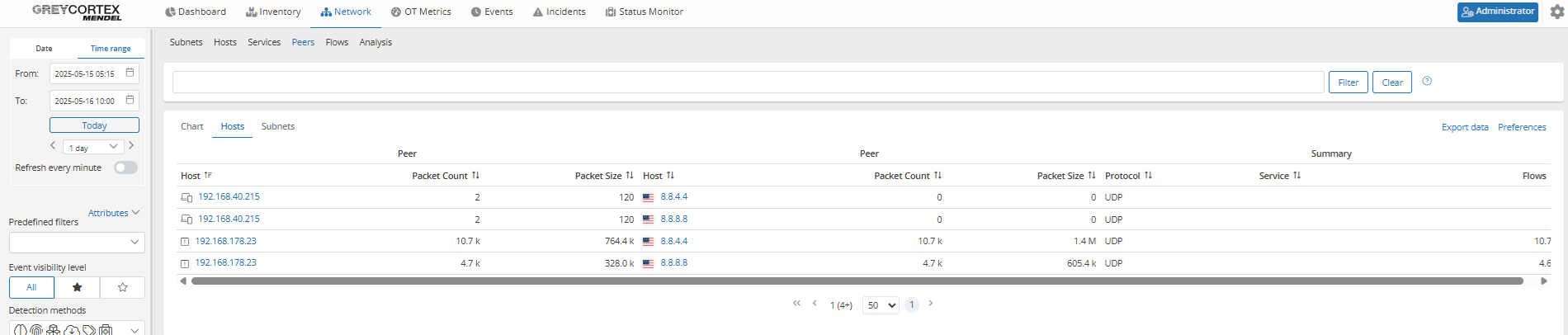
Public DNS usage: By filtering outbound DNS traffic, Mendel reveals which internal devices are using public DNS servers. This allows your analysts to identify whether DNS queries are leaving the network through unapproved resolvers.
In one case, two hosts were detected using Google DNS services: one being a default gateway, and another (192.168.40.215) a standard internal client. Such cases should be reviewed against DNS usage policies to ensure compliance.
Policy violation: Unauthorized DHCP Servers
Relevant for NIS2
This policy ensures that only approved DHCP servers operate in the network. Unauthorized DHCP servers can assign incorrect configurations, enable man-in-the-middle attacks, or disrupt connectivity.
Validation with Mendel
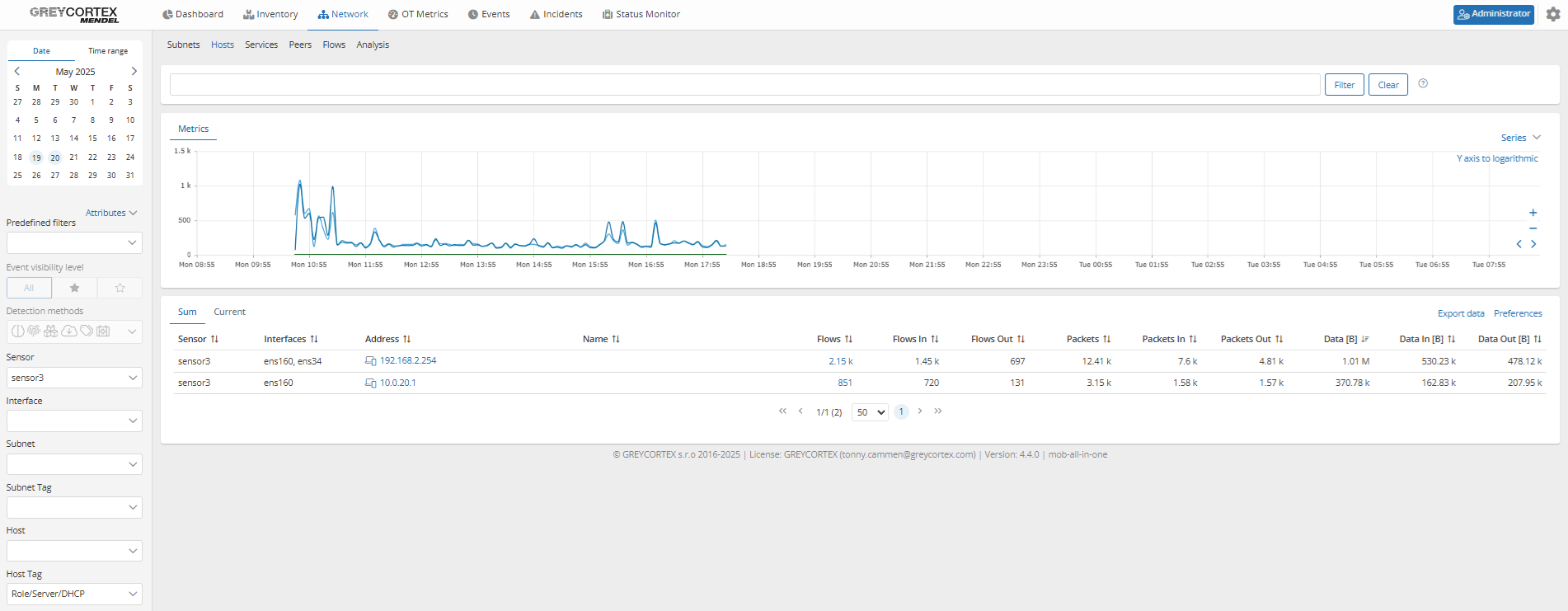
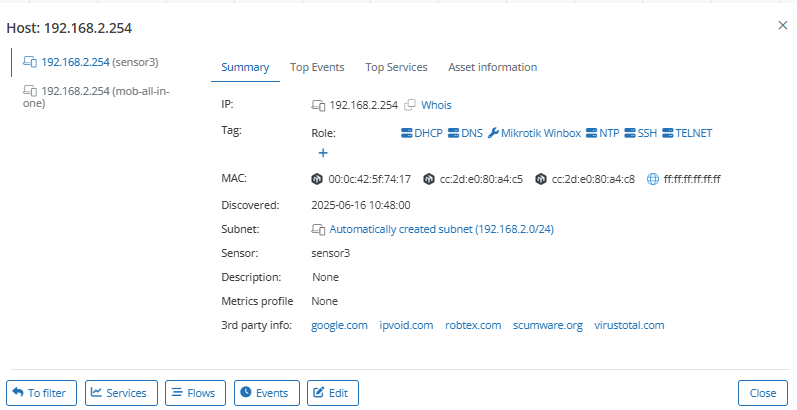
Mendel automatically detects new DHCP servers in your network and generates an event. In addition, it lists all DHCP servers by filtering hosts with the tag Role/Server/DHCP, helping your analysts verify whether each one is authorized or misconfigured. Drilling down on each IP reveals additional services and host behavior for deeper inspection.
For example, device 192.168.2.254 was found running multiple services, including DHCP, NTP, DNS, SSH, TELNET, and Mikrotik Winbox. This suggests it may be a router or a misconfigured network appliance.
From Visibility to Accountability
Enforcing internal rules only matters if those rules are visible and actionable. Without continuous policy monitoring, organizations like yours risk overlooking gaps that can lead to misconfigurations or downtime. Mendel helps you by aligning internal visibility with real-time behavior, enabling your teams to improve incident response, reduce alert fatigue, and maintain control over your environment.
In the next part, we’ll explore how Mendel validates encryption policies, user identity enforcement, and application-level restrictions, which are critical areas for maintaining compliance and reducing operational risk.
Want to evaluate your own network? Request a security audit with Mendel.
Categories
- Company News (35)
- Product News (27)
- IT/OT Security (39)
- Webinars (6)