Ransomware has been around for years, yet it remains the most disruptive cyber threat organizations face. The reason is simple: attackers have grown smarter, more targeted,
and far more organized.
In 2017, WannaCry swept the globe indiscriminately. In 2021, the Colonial Pipeline attack showed how a single campaign could halt critical infrastructure and cause nationwide disruption.
Fueling this evolution is the rise of Ransomware-as-a-Service. Attack kits can now be purchased on underground markets, lowering the bar for entry. Competitors, political actors, or anyone seeking fast money can launch professional-grade attacks without deep technical skills.
For defenders, the lesson is clear: ransomware is no longer a passing trend but an established business model. Detecting it early means looking where attackers cannot hide — in the network traffic that always betrays their presence.
Traditional Security Tools and Their Limits
Most organizations rely on firewalls and endpoint protection platforms (EPP/EDR) as their main defenses. These tools block known threats, detect malicious behavior on laptops and servers, and help analysts respond quickly. For many types of attacks, they remain essential.
The problem comes with everything that endpoint agents cannot cover. Printers, scanners, IP phones, cameras, or industrial OT / IoT devices, typically running on outdated systems and often not possible to be patched or updated. Because they don’t support endpoint agents, they become weak spots in the network. Attackers know this and they exploit these unmanaged assets to move further inside.
That’s the ceiling of traditional tools, they secure what they can run on, but they leave blind spots everywhere else, and those blind spots are exactly where ransomware actors look for opportunities.
Network Visibility Matters
Ransomware may enter through many paths, but it cannot operate without leaving a footprint in your network traffic. Whether it is an unexpected data transfer, a connection to an unusual external server, or the sudden use of a new protocol, these are all signals that something could be wrong.
Unlike endpoint tools, network monitoring covers everything, managed laptops and servers as well as printers, cameras, IoT devices, and legacy systems that are not able to run agents. It gives you the one vantage point attackers cannot avoid.
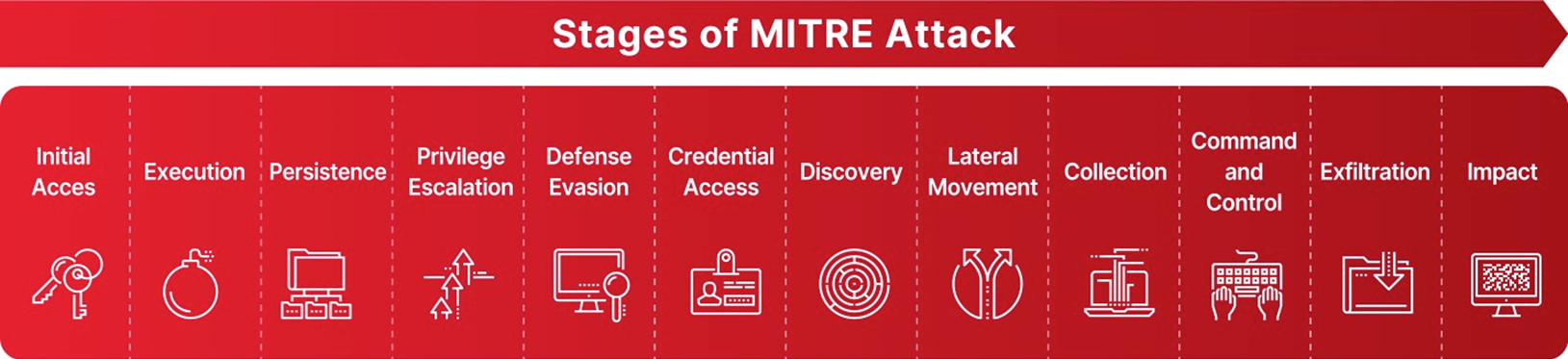
Ransomware: Step by Step with MITRE ATT&CK
Ransomware attacks unfold gradually, moving through distinct stages. Nearly every step leaves a detectable trace in your network traffic that can be used for early detection.
Stage: Initial Access
The attacker gains an initial foothold on a device. This may involve exploiting a known or unknown vulnerability, a misconfiguration, brute-force attack, or stolen credentials. In every case, a new and unusual communication vector appears that can be observed in the network.
Stage: Execution
The attacker runs the tools or scripts needed for the next phases, often downloading loaders or exploit kits. These activities are accompanied by network traffic that stands out as abnormal.
Stage: Persistence
To maintain access, the attacker may hijack code, create new accounts, enable RDP, or modify SSH keys. Each of these actions creates new services or unexpected connections, leaving clear traces in the network.
Stage: Privilege Escalation and Credential Access
Attackers attempt to elevate their privileges and harvest credentials, typically on a compromised host. Once tokens, NTLM hashes, or domain admin credentials are used for authentication, the activity becomes visible in the network.
Techniques such as Man-in-the-Middle, LLMNR poisoning, or dictionary attacks also leave recognizable traces in the network.
Stage: Discovery and Lateral Movement
The attacker maps the environment and searches for new targets. This includes network scans, port knocking, or service enumeration, followed by lateral movement using SMB, remote code execution, or RDP. Each activity generates clear signals in traffic patterns.
Stage: Command and Control (C&C)
Establishing contact with a command server is a critical phase. It may involve suspicious IP addresses or legitimate services that evade blacklists. Often, attackers use periodic beaconing or disguise traffic as normal communications. Even so, these techniques produce detectable patterns in network behavior.
Stage: Exfiltration
The final stage is data theft. It shows up as abnormal data volumes, unusual transfer directions, or the use of legitimate cloud services such as Dropbox or OneDrive. These activities signal exfiltration of sensitive data or company know-how.
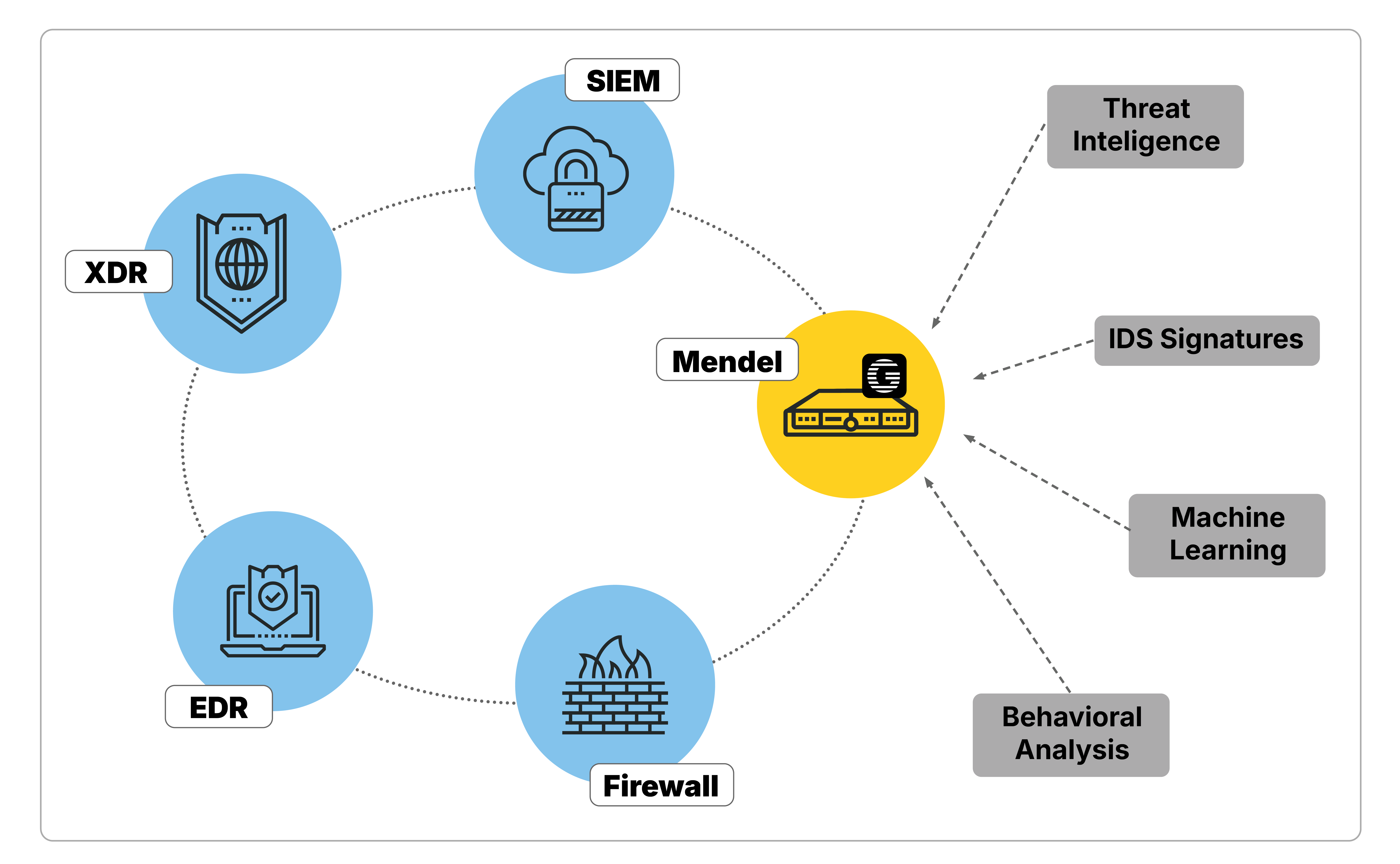
Detect Ransomware with Mendel
Almost every stage of a ransomware attack leaves footprints in your network traffic and GREYCORTEX Mendel is designed to reveal them. Mendel monitors the behavior of your entire infrastructure, not just endpoints. It uses a mix of machine learning and behavioral analysis to model the behavior of your network, its subnets, and each device individually. Based on this analysis, Mendel can distinguish between malicious activity, potential threats, anomalous behavior, and legitimate traffic.
This approach is invaluable where endpoint protection cannot be deployed. That is why Mendel has become an important component of modern cybersecurity ecosystems. It also integrates smoothly with XDR platforms, expanding their detection and response capabilities with detailed network insights.
Staying Secure After the Attack
Stopping ransomware is only part of the job. The bigger challenge is making sure attackers did not leave a way back in. Hidden backdoors, beaconing traffic, or “keep alive” connections can quietly remain in the network long after the initial threat is blocked.
Mendel helps with compromise assessment by continuously monitoring post-incident traffic and exposing these traces. Whether it is covert communication with a command-and-control server, unusual persistence mechanisms, or unexplained connections between internal hosts, Mendel verifies that the environment is truly clean.
This ongoing visibility strengthens recovery efforts and ensures long-term resilience. As part of a wider cybersecurity ecosystem, Mendel not only helps you detect and stop active attacks but also provides the assurance that systems remain secure after remediation.
Make sure nothing is left behind. Run a security audit with GREYCORTEX Mendel and regain full confidence in your network.
Categories
- Company News (35)
- Product News (27)
- IT/OT Security (39)
- Webinars (6)