Secure Your Smart Metering (AMI) Infrastructure
Network Visibility for Resilient AMI Operations
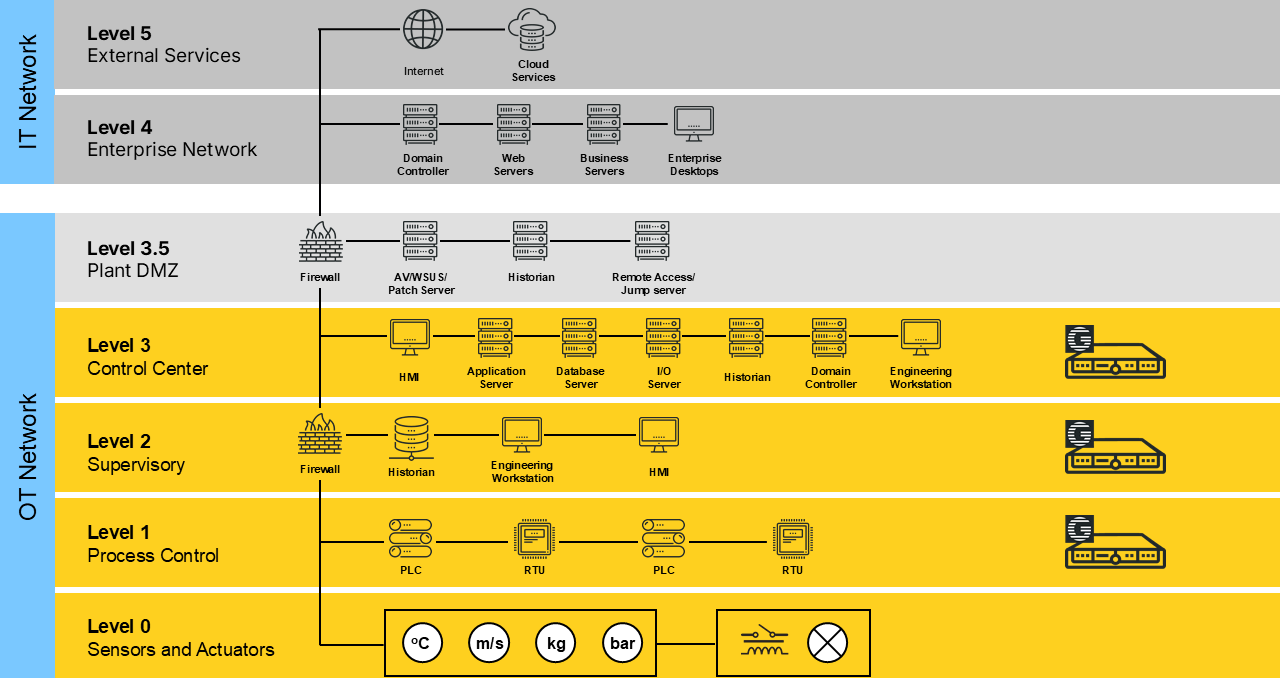
Advanced Metering Infrastructure (AMI) is the digital backbone of modern utility services, combining smart meters, communication networks, and central management systems to measure consumption and transmit data in near real time. It supports critical functions such as billing, outage detection, and demand management. As AMI deployments scale to millions of connected devices, utilities face growing challenges in maintaining security, reliability, and regulatory compliance. Full visibility into AMI network communication is therefore essential for protecting operations and maintaining trust.
To manage large-scale AMI environments effectively, utilities need a clear view of how meters, concentrators, and head-end systems communicate across the network. The monitoring approach must be fully passive, with no impact on daily operations, while enabling teams to detect anomalies early, maintain service stability, and meet compliance requirements with confidence.
Address your challenges with Mendel
- Detect anomalies and threats across IT and OT systems, including in communication AMI network
- Ensure continuous operations through passive, non-intrusive monitoring
- Simplify compliance with NIS2 and national regulations for the energy sector
- Scale seamlessly as your network and number of connected assets grow
Single Security Solution for IT & OT Environments
Threat and Anomaly Detection
Identify new or unauthorized devices, first-seen communication, and traffic outside approved network paths. Mendel lets you track changes in device parameters, unusual command activity, and abnormal communication patterns.
Asset Management
Discover and classify all connected assets, including smart meters, concentrators, and control systems. Using Mendel, automatically identify vendor details, firmware versions, and configuration changes.
Protocol Visibility
Analyze communication between smart meters and utility systems with extended DLMS/COSEM protocol details. Mendel lets you track parameter changes, unexpected commands, and communication patterns that deviate from normal operation.
Access Management
Monitor all access to your network, including remote connections via VPN, and verify that they follow established security policies. Mendel shows you which systems external contractors connect to, what data they access, and which configuration changes they perform.

Explore AMI Network Detection with Mendel

Passive, agentless deployment
Collect and analyze network data without scanning or installing agents on devices.

Audit-ready evidence
Facilitate compliance through real-time monitoring and automatic data retention.

Scale without disruption
Expand monitoring from individual substations to large smart meter networks with a flexible, scalable architecture.
Meet Mendel
GREYCORTEX Mendel is a Network Detection and Response (NDR) solution for IT and OT environments. It provides you real-time insight into communication between smart meters, concentrators, and control systems – detecting anomalies, unauthorized activity, and configuration changes before they impact operations.
Built for non-intrusive monitoring, Mendel helps utilities and energy providers secure their smart-meter infrastructure, maintain compliance, and support stable, continuous service.
How Mendel Is Deployed
Mendel is deployed passively using SPAN or TAP ports, ensuring zero impact on your critical operations or network performance. It can also process flow data (IPFIX, NetFlow, NetStream) and application logs to extend visibility beyond mirrored traffic.
All collected data integrates directly with your SIEM, SOAR, or ticketing systems via syslog, providing seamless connection to existing cybersecurity workflows.